The managed security domain has been crucial in helping small- and medium-sized businesses and large enterprises to counter the ever-rising cyber threats. For example, more Swiss organizations are often overwhelmed by data, network, and system security demands and are turning to external service providers, especially those in the managed security services sector. In addition, an expanding threat surface, cybersecurity skills shortage, and lack of proper resources have forced most Swiss authorities and organizations to adopt managed security services for technical security assistance and strategic direction.
However, countries worldwide strive to develop and retain their unique cybersecurity initiatives in the current borderless threat environment. Managed security services are cross-border, where a Swiss company can outsource cybersecurity functions to a firm in a different country, implying that its data is stored and processed in a foreign nation.
This is where cyber sovereignty comes in – where a nation has control of the data and security of its cyberspace. It is essential to assess Switzerland's cyber sovereignty within the managed security domains to understand the importance of controlling the security of the country's cyberspace. Switzerland's cyber sovereignty depends on factors like reliance on foreign technological solutions, existing cyber resilience capabilities, and the complexity of the country's cyber governance environment.
Swiss sovereignty is the backbone of effective cybersecurity strategies
Threat actors are continually stepping up their targeted and malware attacks resulting in far-reaching impacts for the victims. In Switzerland, 61% of businesses rank cyber attacks as the risks they fear the most in 2022. Despite this, a survey found that only 58% of Swiss companies understand the needs and value of equipped cybersecurity teams, leaving most businesses to outsource their cybersecurity processes. The sovereignty of such managed security services is important when considering your organization's cybersecurity solutions for the following reasons.
Trust – an important factor when choosing a managed security provider
Above all else, opting to outsource to a sovereign managed security provider implies ensuring transparency and trust and preventing risks that rogue providers will exploit your data for malicious reasons. Also, sovereign-managed security services provide access to well-controlled and regulated sovereign cybersecurity solutions and personnel, mitigating the risks of attacks and being compromised by foreign entities. Choosing sovereign managed security services ensures a defense-in-depth security approach without weak links to prevent cybersecurity scares and failures.
At the same time, sovereign cybersecurity services are equally important in preventing risks like corporate espionage and interference. In a recent case, a Chinese group called Winnti was investigated for its role in conducting large-scale corporate espionage in Asia, the US, and Europe through managed services. Such occurrences can also affect companies reliant on foreign-managed security services. Retaining your digital independence by choosing a sovereign Swiss-managed security provider enables autonomous and local response to cyber incidents, protecting you from possible acts of corporate espionage and spying.
Besides, Switzerland is among the European nations that have legislated and enforced numerous compliance regulations in the recent past to ensure data security and data privacy. However, data protection laws differ from country to country, meaning that foreign managed security providers comply with different regulations when processing and securing data from a Swiss organization. Therefore, the choice of a sovereign managed security service supports native compliance with the relevant cybersecurity standards and regulations. Furthermore, this equips you with the regulatory requirements to deliver secure access to data, operating systems, and information systems.
In other words, there is an urgent need for Swiss companies to outsource to more trusted managed security providers, especially with the proliferation of managed security providers all over the world.
Investing in the Swiss managed security services sector
Switzerland's cybersecurity community depends on various assets to provide organizations with a resilient and reliable cyber environment. Therefore, it is important to enable the Swiss cybersecurity industry to make proper choices by expanding the locally available managed security services solutions. Furthermore, investing in Switzerland's managed security services sector ensures that consumers and end-users about sovereign and locally sources services can select their sovereign managed providers of choice as a basic minimum, which goes hand-in-hand with creating awareness of same Swiss companies outsourcing their services also to sovereign managed security service providers.
More generally, investment in managed security services through education and dedicated funds is important in growing the sector to encourage sovereign startups and reduce reliance on foreign managed security providers. With the effective cooperation between Swiss players and the involvement of the managed security services sector, more Swiss companies can choose sovereign managed cybersecurity solutions, providing them with increased sovereign control of their cybersecurity procedures and, at the same time, provide them with optimal and compliant data, network, cloud, IoT, and operational technology security.
Why does cyber sovereignty matter?
Managed security services remain the go-to for Swiss companies lacking adequate cybersecurity technologies and personnel. Unfortunately, foreign managed security providers process and store data across Switzerland's geographical borders and often use foreign technology solutions, thus raising concerns over technological, digital, and data sovereignty. Cyber sovereignty means the degree to which an organization has control over the data it produces or the cybersecurity technologies it uses to defend itself. Three primary factors influence the sovereignty of a managed security service provider:
- Geographical location: Where does a managed security provider store your data, and where does it develop cybersecurity technologies and harden them to ensure resiliency?
- Operational factor: Who has access to and uses your data and designed the cybersecurity technologies you operate to secure your organization?
- Cybersecurity regulations: What are the regulations and laws that apply to your data, and how do they affect you if the providers' regulations are different from those in Switzerland?
As many Swiss companies embrace managed security services, they must evaluate their data and technological sovereignty risks. For instance, when a company delegates cybersecurity functions and processes to a foreign managed service provider, it places itself at the security provider's mercy despite the provider's regulatory authority. On the other hand, choosing a trusted sovereign managed security provider gives you more control over your data and promises increased oversight and security due to compliance with sovereign data protection regulations. More importantly, a sovereign managed security provider provides a competitive advantage since it puts data sovereignty at the core of your digital transformation efforts, enabling trust and transparency.
Extraterritorial laws introduce risks to your organization
When you choose a foreign managed cybersecurity provider, it is governed by the laws existing in their country. Thus, the global debate on cyber sovereignty stems from the various extraterritorial laws that may introduce specific risks to your organization. You may not be aware of foreign laws that adversely impact your business. For instance, the US Cloud Act permits US security agencies to order your managed security provider to disclose your organization's data if there is an ongoing criminal investigation for US-based companies and organizations in foreign nations. The act may require you to disclose sensitive information, such as customer data, which may cause your customers to lose trust in your ability to protect their data from unauthorized access.
Data sovereignty is key to enhanced privacy and security
Data sovereignty means the legal frameworks implemented to manage your data in a specific jurisdiction, such as within Swiss borders. When choosing a managed security provider, you must deal with a firm you trust granting you control over the use, storage, or deletion of your data. According to a recent study, 87% of the participants said they would be reluctant to allow companies with concerning security practices to manage their data, and 71% would terminate business engagements if an organization gives access to customer data without their permission.
Choosing a sovereign managed security provider enables data sovereignty, which allows the data owner to exert jurisdictional control of their data. This is advantageous since it enables companies to develop confidentiality and security policies compliant with the prevailing data regulations and that meet their customers' expectations regarding data security and privacy. Moreover, data sovereignty minimizes the possibility that your data may be leaked to foreign institutions with zero guarantees of any legal solution.
How can you achieve data sovereignty?
A possible solution is that all Swiss companies, down to public bodies, become fully independent from foreign managed security services and infrastructure and exclude foreign actors from providing any cybersecurity functions. However, such a model is often unrealistic since data and technological sovereignty do not imply protectionism; rather, it should be your ability to shape your digital and cybersecurity transformation plans in a self-determined method. A more realistic approach would be to promote Swiss managed security services competencies while acknowledging certain dependencies with foreign managed security providers.
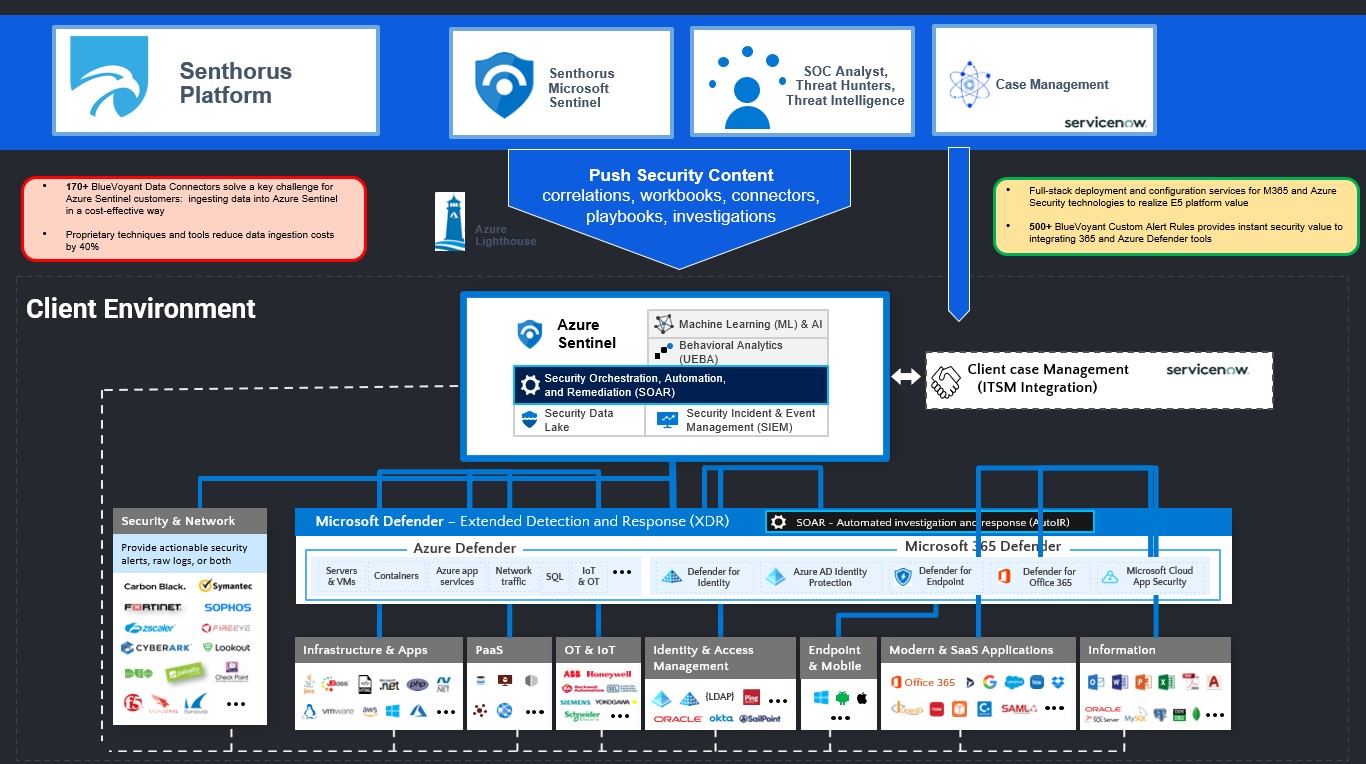

Cybersecurity sovereignty with ELCASecurity
ELCASecurity Managed Services helps reduce internal complexity and provides live alerts and event dependencies for IT endpoints and the cloud infrastructures.
A partnership between ELCA and BlueVoyant brings together years of experience in IT and Managed Detection and Response. As Senthorus, ELCA and BlueVoyant address your needs on a bespoke basis. Senthorus customers benefit from state-of-the-art protection, delivered by an independent, trusted Swiss company, with all customer data kept securely in Switzerland.
The Senthorus Security Operations Center (SOC) will be based in Switzerland, operated 24/7, and all data is processed and stored locally in Switzerland. This new home of a group of specialists in cyber-defense means we can offer you an integrated security service with Managed Detection and Response while also being close at hand to offer you Incident response.
